Enterprise DAM security demands comprehensive protection beyond basic file storage.
- Multi-layered security architecture combining encryption, access controls, and compliance frameworks
- AI-powered governance to detect emerging threats and manage autonomous AI risks
- Real-time monitoring with comprehensive audit trails and incident response capabilities
- Industry-specific compliance support for HIPAA, GDPR, SOC 2, and ISO 27001 requirements
Organizations need secure DAM systems that evolve with emerging threats while maintaining operational efficiency.
Your digital assets are valuable and vulnerable. Product designs, proprietary research, customer data embedded in marketing materials – all of it needs protection beyond what basic cloud storage can provide. AI data leaks are a primary concern for 69% of organizations, yet 47% lack security controls specifically designed for AI.
The challenge isn’t just protecting assets from external threats anymore. Modern enterprises need to secure their digital asset management operations against ransomware attacks, insider threats, emerging AI governance risks, and complex regulatory requirements. Traditional file sharing and basic cloud storage simply can’t meet these sophisticated security demands.
What Makes a DAM System Secure for Enterprises?
A truly secure DAM system operates on multiple defensive layers, each designed to protect different aspects of your digital assets throughout their lifecycle. When done right, security in DAM covers data integrity, availability, compliance, and governance across distributed teams and complex workflows.
Enterprise DAM security rests on three core principles: confidentiality, integrity, and availability.
- Confidentiality means only authorized users can access sensitive assets through robust authentication and access controls.
- Integrity protects assets from unauthorized changes through version control and audit trails.
- Availability guarantees authorized users can access critical assets when needed, even during security incidents or system failures.
The most effective secure DAM systems use defense-in-depth strategies – multiple security technologies and processes working together to create overlapping barriers. No single security measure is foolproof, so layered controls work together to minimize risk and contain potential breaches before they cause real damage.

What Technical Security Controls Are Essential for Enterprise DAM?
Let’s talk about the technical safeguards that protect your assets both at rest and in transit.
Enterprise-grade encryption uses AES-256 standards for stored assets and TLS 1.3 for data transmission. Even if storage systems are compromised, the encrypted data remains protected and unusable to unauthorized parties.
Multi-factor authentication is another critical control, beyond simple username-password combinations. Advanced implementations integrate with existing enterprise identity providers and support various authentication methods, including hardware tokens, biometric verification, and certificate-based authentication. This layered approach reduces the risk of credential-based attacks.
Role-based access control (RBAC) is the operational backbone of secure DAM systems. Instead of managing permissions for individual users, RBAC assigns rights based on job functions. A marketing manager might have upload and approval rights for campaign assets, while external contractors get view-only access to specific project folders. This granular control extends to the asset level, so you can restrict access to confidential materials while keeping collaboration efficient.
Network security controls provide additional protection through firewall configurations, intrusion detection systems, and network segmentation. Modern secure DAM systems often implement zero-trust architecture principles, treating every access request as potentially suspicious until properly verified and authorized.
Real-time monitoring detects unusual access patterns, bulk download attempts, or unauthorized sharing activities. These systems generate alerts for suspicious behavior while maintaining detailed audit logs for forensic analysis and compliance reporting.
How Do Compliance Frameworks Integrate with Secure DAM Systems?
Most enterprises need to comply with multiple regulatory frameworks, each with specific requirements for data protection and asset management. The key to effective compliance is choosing DAM systems that align with comprehensive frameworks rather than requiring separate solutions for each standard.
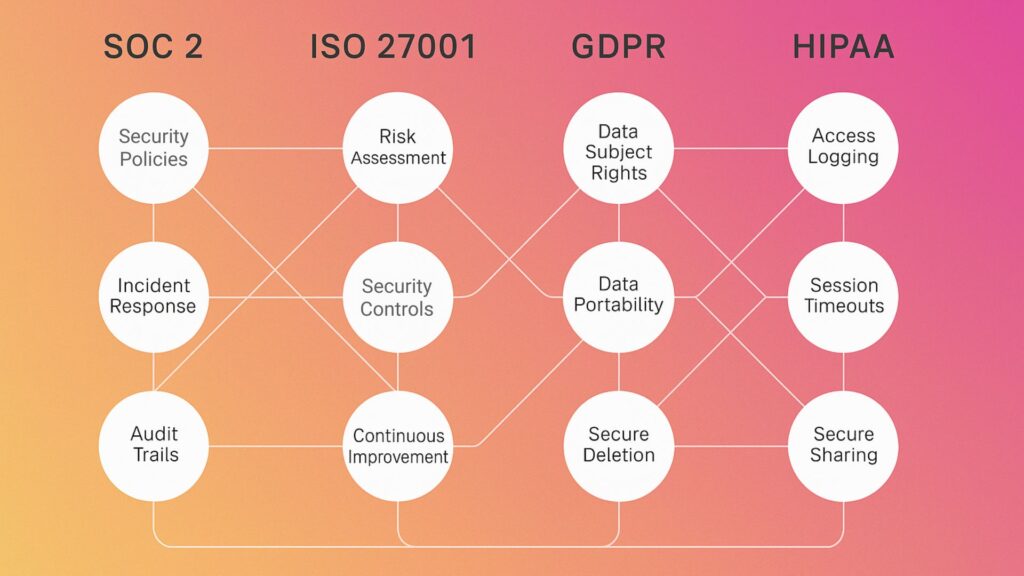
SOC 2 compliance focuses on security, availability, processing integrity, confidentiality, and privacy controls. For DAM systems, this translates to documented security policies, regular penetration testing, incident response procedures, and continuous monitoring capabilities. Organizations pursuing SOC 2 certification need DAM platforms that provide detailed audit trails and security reporting features that can withstand independent assessment.
ISO 27001 provides a systematic approach to managing information security through an Information Security Management System (ISMS). DAM systems supporting ISO 27001 compliance include comprehensive risk assessment tools, security control implementation tracking, and continuous improvement processes. The emphasis on risk-based security aligns well with enterprise DAM needs for protecting varying levels of sensitive content.
GDPR compliance is essential when DAM systems store or process personal data from EU citizens. Consider marketing assets containing customer images, behavioral data, or any identifiable personal information. Compliant DAM systems must support data subject rights, including access requests, data portability, and the “right to be forgotten” through secure deletion capabilities.
HIPAA requirements apply when healthcare organizations use DAM systems for medical imaging, patient education materials, or any content containing protected health information. Beyond standard security controls, HIPAA-compliant DAM systems must provide detailed access logging, automatic session timeouts, and secure sharing capabilities that maintain audit trails for all patient data interactions.
The smart move? Choose DAM platforms that align with multiple frameworks simultaneously. There’s approximately 80% overlap between ISO 27001 and SOC 2 criteria, which means you can streamline compliance efforts rather than managing separate systems for each requirement.
How Are AI Security Risks Changing DAM Requirements?
Artificial intelligence in enterprise content operations has introduced entirely new security risks that traditional DAM security models weren’t designed to handle. Organizations now face challenges from “shadow AI” (unsanctioned AI tools employees use without IT approval) as well as the security implications of AI-generated content and autonomous AI agents operating within content workflows.

AI-powered content creation tools can inadvertently expose sensitive data used in training prompts or generate content that looks authentic but violates copyright or compliance policies. Secure DAM systems now need AI content detection capabilities that can identify artificially generated assets and trigger appropriate review workflows before publication.
Agentic AI systems that can autonomously access, modify, and distribute content create new insider threats. These AI agents operate at machine speed and scale, potentially amplifying security breaches. Organizations must develop AI-specific governance frameworks that address autonomous decision-making, chained vulnerabilities, and accountability challenges.
Modern secure DAM systems are implementing AI governance controls, including model provenance tracking, content authenticity verification, and automated policy enforcement for AI-generated assets. These systems monitor AI interactions with digital assets, ensuring that artificial intelligence tools comply with organizational policies and regulatory requirements.
Data governance for AI training is vital when organizations use their DAM content to train custom AI models. Secure systems implement data classification policies that prevent sensitive or personally identifiable information from being inadvertently included in AI training datasets while maintaining audit trails of all AI-related data usage.
What Advanced Enterprise Security Features Should Organizations Expect?
Enterprise-grade digital asset management security goes beyond the basics. We’re talking comprehensive digital rights management, incident response capabilities, and advanced threat detection that maintain security at scale while supporting complex global operations.
Digital rights management (DRM) ensures that protected content remains secure even after distribution. This feature includes automatic watermarking, usage tracking, and remote revocation that prevent unauthorized use of confidential materials. Advanced DRM systems can disable access to distributed content if security breaches are detected or employment relationships end.
Comprehensive audit trails provide the detailed logging necessary for security analysis, compliance reporting, and forensic investigation. Modern systems capture not just who accessed what content but also track content modifications, sharing activities, download patterns, and failed access attempts. This information proves invaluable for detecting insider threats and understanding the full scope of potential security incidents.
Automated incident response contains security breaches through predefined workflows. When suspicious activity is detected, these systems can automatically revoke access credentials, quarantine affected assets, notify security teams, and initiate forensic data collection. This automation reduces response times from hours to minutes, significantly limiting potential damage.
Integration with Security Information and Event Management (SIEM) systems provides centralized security monitoring across enterprise technology stacks. DAM security events feed into broader threat intelligence platforms, enabling correlation with other security data to identify attack patterns that might otherwise go undetected.
Advanced threat intelligence incorporates external threat feeds and machine learning algorithms to identify emerging attack patterns and proactively strengthen defenses. These systems learn normal user behavior patterns and can detect anomalies that might indicate compromised accounts or insider threats.
Essential DAM Security Implementation Best Practices
Implementing comprehensive security in DAM should address both technical controls and operational procedures. These proven practices help organizations establish robust security postures while maintaining operational efficiency:
Implement Zero-Trust Architecture Principles. Treat every access request as potentially suspicious until properly verified. This means requiring authentication and authorization for all users, including those connecting from internal networks. Zero-trust implementations provide enhanced security in DAM through continuous verification and reduced attack surfaces.
Establish Granular Permission Hierarchies. Design role-based access controls that match your organizational structure and content sensitivity levels. Create specific roles for different asset types, project involvement, and geographical locations. Regularly audit and update permissions as organizational needs evolve.
Deploy Multi-Factor Authentication Universally. Require MFA for all DAM access, including API connections and service accounts. Implement adaptive authentication that increases security requirements based on access patterns, locations, and asset sensitivity levels.
Maintain Comprehensive Asset Classification Systems. Develop clear guidelines for categorizing content based on sensitivity levels, compliance requirements, and business criticality. Automated classification tools can help maintain consistency across large asset libraries while reducing human error.
Implement Automated Security Monitoring. Deploy real-time monitoring systems that can detect unusual access patterns, bulk downloads, or unauthorized sharing activities. Set up automated alerts for high-risk activities while maintaining detailed logs for investigation and compliance reporting.
Establish Regular Security Training Programs. Educate users on secure asset handling, password hygiene, phishing recognition, and incident reporting procedures. Security-aware users represent the strongest defense against social engineering and insider threats.
Create Comprehensive Backup and Recovery Procedures. Implement automated backup systems with offline storage components to protect against ransomware attacks. Regularly test recovery procedures to ensure business continuity during security incidents.
Conduct Regular Security Assessments. Perform quarterly security audits, annual penetration testing, and ongoing vulnerability assessments. Use findings to continuously improve security controls and update policies based on emerging threats.
Develop Detailed Incident Response Plans. Create specific procedures for different types of security incidents, including data breaches, insider threats, and system compromises. Practice incident response through tabletop exercises and simulations to ensure team readiness.
Maintain Vendor Security Oversight. Regularly assess the security posture of DAM providers, including their compliance certifications, security practices, and incident response capabilities. Require detailed security documentation and regular security reviews as part of vendor management.
How Should Organizations Evaluate Digital Asset Management Security Capabilities?
Evaluating DAM security shouldn’t feel like deciphering a technical manual. You need a platform that protects your assets without slowing down your teams.
Start with a comprehensive security assessment that involves IT, compliance, legal, and business stakeholders. This cross-functional approach ensures your solution meets real-world requirements. Identify potential threats, regulatory needs, and performance expectations early to avoid surprises later.
Vendor transparency is key. Ask for detailed documentation of the platform’s security architecture, including encryption protocols, authentication methods, and incident response procedures. Confirm the provider holds verifiable certifications, such as SOC 2 Type II and ISO 27001, and if applicable, frameworks like FedRAMP or HITRUST. These attestations prove the DAM system has undergone rigorous, independent evaluation.
Look beyond checklists to understand how each vendor handles ongoing protection. What’s their track record for incident response? How quickly do they communicate security advisories? How do they incorporate new standards as threats evolve? A trustworthy vendor will share their approach openly and proactively.
From a technical standpoint, assess whether the system can integrate with your security ecosystem. Modern enterprise DAMs should support API-based integrations with SIEM tools, identity management systems, and other monitoring technologies. Evaluate flexibility for custom policies and configurations to match your internal requirements.
Finally, think about usability alongside control. Even the most secure DAM system fails if users work around it. Evaluate how intuitive the interface feels, whether permissions are easy to manage, and how well the system balances security with user experience. A platform that makes security simple to follow rather than something to avoid will deliver far greater long-term value.
Frequently Asked Questions
How does encryption in DAM systems protect against data breaches? Encryption renders digital assets unreadable to unauthorized parties even if storage systems are compromised. Modern DAM systems use AES-256 encryption for stored assets and TLS 1.3 for data transmission. Even if attackers gain access to encrypted files, they cannot read the content without proper decryption keys, which are stored separately and protected by additional security controls.
What’s the difference between role-based and attribute-based access control in DAM? Role-based access control assigns permissions based on job functions, while attribute-based access control makes decisions based on multiple factors, including user attributes, asset characteristics, and environmental conditions. RBAC works well for stable organizational structures, while ABAC provides more flexibility for dynamic environments where access requirements frequently change based on project involvement, location, or time-sensitive factors.
How do organizations maintain DAM security during remote work scenarios? Remote digital asset management security relies on strong authentication, encrypted connections, and endpoint protection. Organizations typically implement VPN requirements, device management policies, and additional monitoring for remote access patterns. Cloud-based DAM systems often provide better security for remote work than on-premises solutions due to their built-in security infrastructure and global access capabilities.
What should organizations do if they discover unauthorized access to their DAM system? Immediate incident response should include isolating affected systems, preserving forensic evidence, notifying relevant stakeholders, and beginning damage assessment. Organizations should follow predetermined incident response plans that include specific procedures for DAM security breaches, including notification requirements for compliance frameworks and customers who may be affected by the incident.
Make Your Enterprise DAM System More Secure
Digital asset security demands comprehensive strategies that protect valuable enterprise content while enabling productive collaboration and innovation. The most effective approaches combine multiple technical controls, compliance frameworks, and operational procedures into cohesive security architectures that can evolve with changing threat landscapes and emerging technologies.
Aprimo provides comprehensive security features designed specifically for large-scale organizations with complex compliance requirements. With industry-leading certifications, AI-powered governance capabilities, and proven enterprise security architecture, we help organizations protect their most valuable digital assets while maintaining operational efficiency. Get started with a security-focused DAM assessment to discover how comprehensive protection can enhance your content operations strategy.


